Year: 2018

Cyber Threats to Watch in 2019: Key Takeaways from our webinar with the FBI Cyber Squad
December 20, 2018 | 5 Min Read

Cyber Threats to Watch in 2019: Key Takeaways from our webinar with the FBI Cyber Squad
December 20, 2018 | 5 Min Read

The Most Popular Security Blog Topics of 2018
December 18, 2018 | 3 Min Read

ShadowTalk Update – 17.10.2018
December 17, 2018 | 3 Min Read
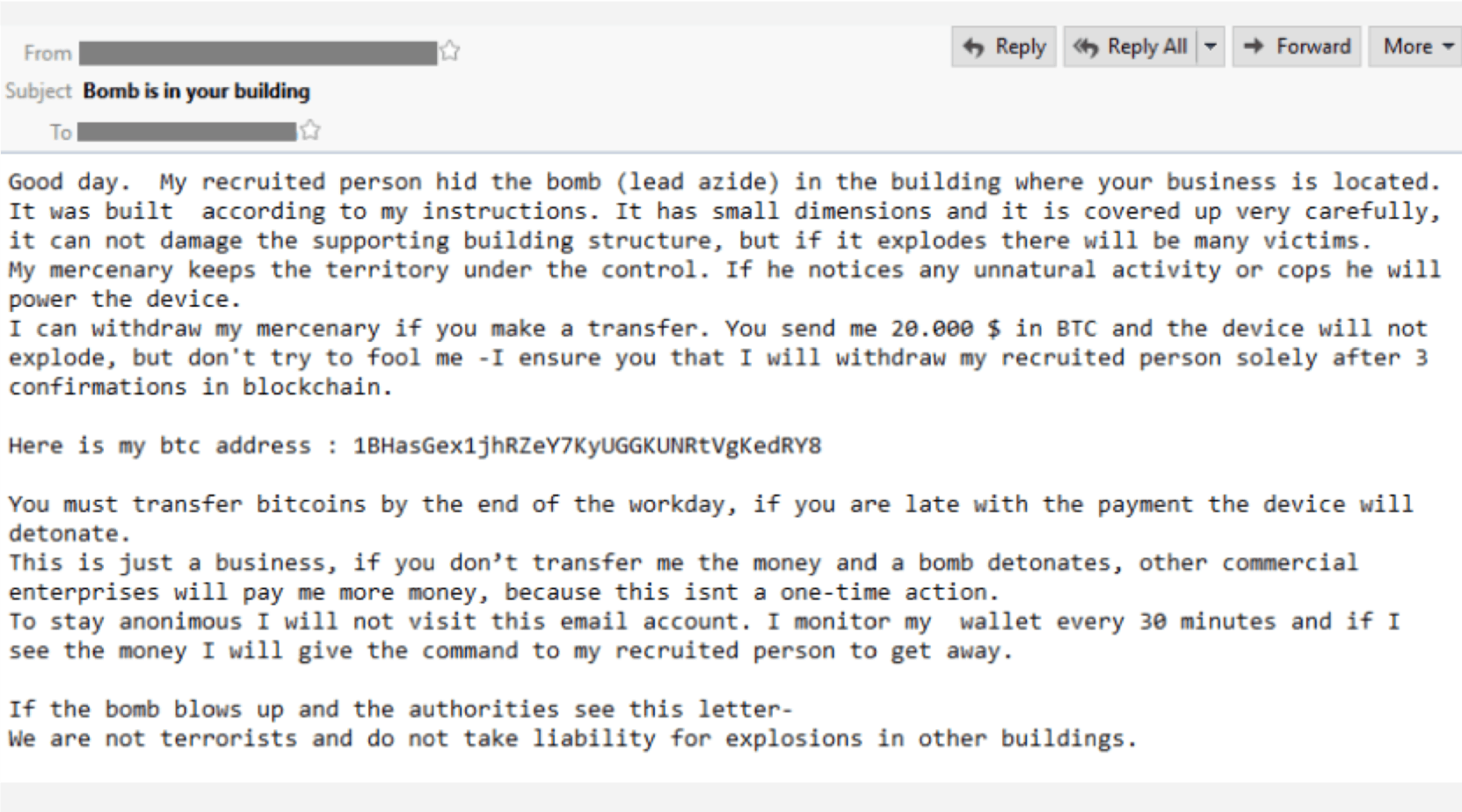
Bomb Threat Emails: Extortion Gets Physical
December 14, 2018 | 4 Min Read

Tackling Phishing: The Most Popular Phishing Techniques and What You Can Do About It
December 12, 2018 | 8 Min Read
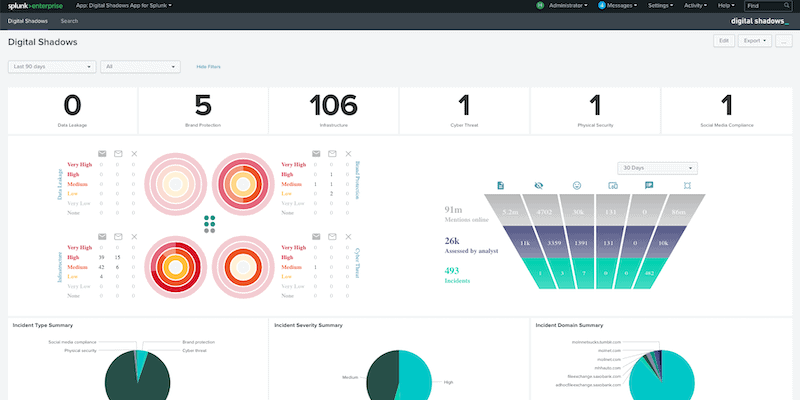
Digital Shadows New Integration for Splunk
December 10, 2018 | 3 Min Read

ShadowTalk Update – 12.10.2018
December 10, 2018 | 3 Min Read
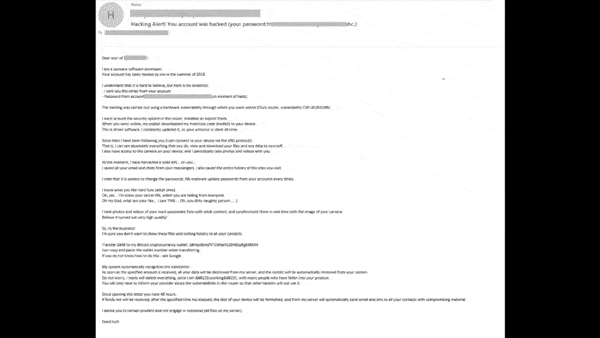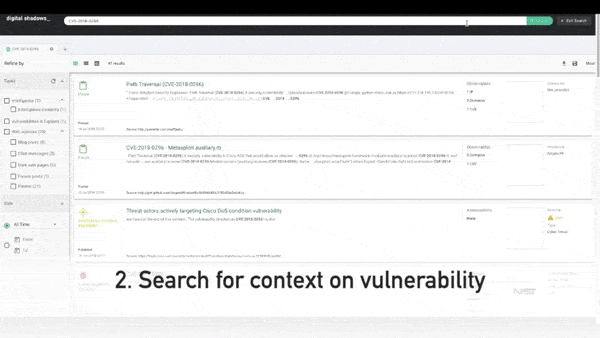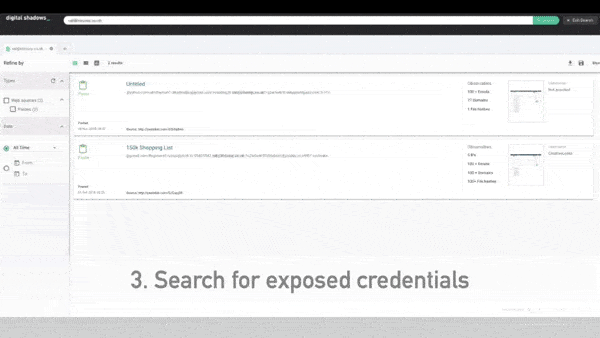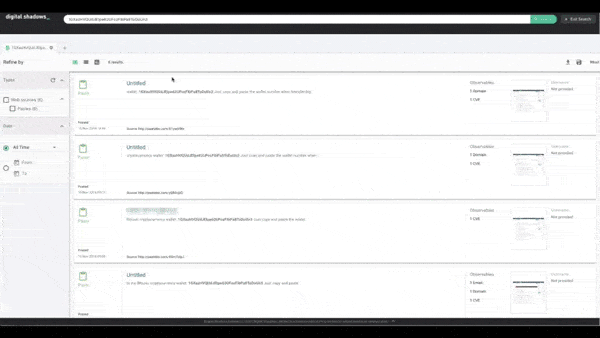
Using Shadow Search to Power Investigations: Sextortion Campaigns
December 6, 2018 | 3 Min Read

2019 Cyber Security Forecasts: Six Things on the Horizon
December 5, 2018 | 9 Min Read

ShadowTalk Update – 12.03.2018
December 3, 2018 | 3 Min Read
Threat Actors Use of Cobalt Strike: Why Defense is Offense’s Child
November 29, 2018 | 5 Min Read

Mapping the ASD Essential 8 to the Mitre ATT&CK™ framework
November 27, 2018 | 3 Min Read

ShadowTalk Update – 11.26.2018
November 26, 2018 | 3 Min Read

Black Friday and Cybercrime: Retail’s Frankenstein Monster
November 20, 2018 | 5 Min Read

Sextortion 2.0: A New Lure
November 20, 2018 | 4 Min Read

ShadowTalk Update – 11.19.2018
November 19, 2018 | 2 Min Read

Law Firm Uncovers Exposed Sensitive Details About Top Attorney Online
November 15, 2018 | 2 Min Read

A Look Back at the ENISA Cyber Threat Intelligence-EU Workshop 2018
November 13, 2018 | 5 Min Read

ShadowTalk Update – 11.12.2018
November 12, 2018 | 2 Min Read

To Pay or Not to Pay: A Large Retailer Responds to DDoS Extortion
November 8, 2018 | 3 Min Read
Security Analyst Spotlight Series: Adam Cook
November 7, 2018 | 6 Min Read

ShadowTalk Update – 11.05.2018
November 5, 2018 | 3 Min Read

81,000 Hacked Facebook Accounts for Sale: 5 Things to Know
November 2, 2018 | 5 Min Read

Choosing the Right Cyber Security Partner for your Business: A glimpse through Digital Logistix journey searching for a Digital Risk Protection Solution
October 31, 2018 | 3 Min Read

The Dark Web: Marketers’ Trick or Threat Intelligence Treat?
October 31, 2018 | 5 Min Read

ShadowTalk Update – 10.29.2018
October 29, 2018 | 3 Min Read

Cyber Security Awareness Month: Week 4 – Privacy
October 25, 2018 | 6 Min Read

Bank Discovers Customer Credit Card Numbers Traded Online
October 23, 2018 | 3 Min Read

ShadowTalk Update – 10.22.2018
October 22, 2018 | 3 Min Read

Cyber Security Awareness Month: Week 3 – Recognize Cyber Scams
October 19, 2018 | 7 Min Read

12.5 Million Email Archives Exposed: Lowering the Barriers for BEC
October 18, 2018 | 4 Min Read

Cyber Security Awareness Month: Week 3 – It’s Everyone’s Job to Ensure Online Safety at Work
October 17, 2018 | 7 Min Read

ShadowTalk Update – 10.15.2018
October 15, 2018 | 3 Min Read

Cyber Security Awareness Month: Week 2 – Aiming for Apprenticeships
October 11, 2018 | 5 Min Read
Phishing Site Impersonates Financial Services Institution
October 10, 2018 | 3 Min Read
33,000 Accounting Inbox Credentials Exposed Online: BEC Made Easy
October 9, 2018 | 4 Min Read

ShadowTalk Update – 10.08.2018
October 8, 2018 | 3 Min Read
Business Email Compromise: When You Don’t Need to Phish
October 4, 2018 | 4 Min Read
Cyber Security Awareness Month: Week 1 – Credential Hygiene
October 3, 2018 | 5 Min Read

Security Analyst Spotlight Series: Christian Rencken
October 2, 2018 | 5 Min Read

ShadowTalk Update – 10.01.2018
October 1, 2018 | 3 Min Read
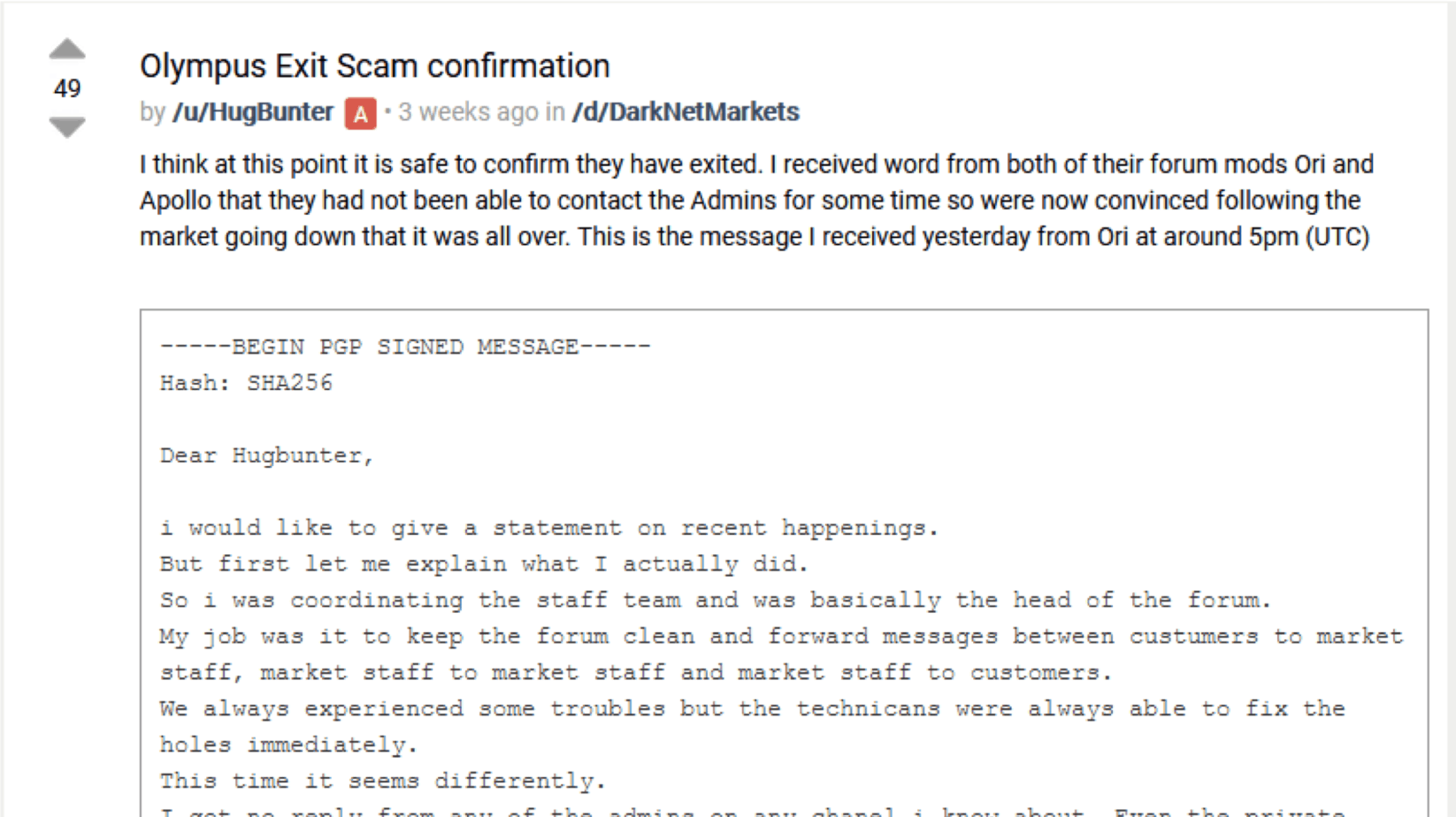
Cybercriminal Marketplaces: Olympus Has Fallen
September 28, 2018 | 5 Min Read
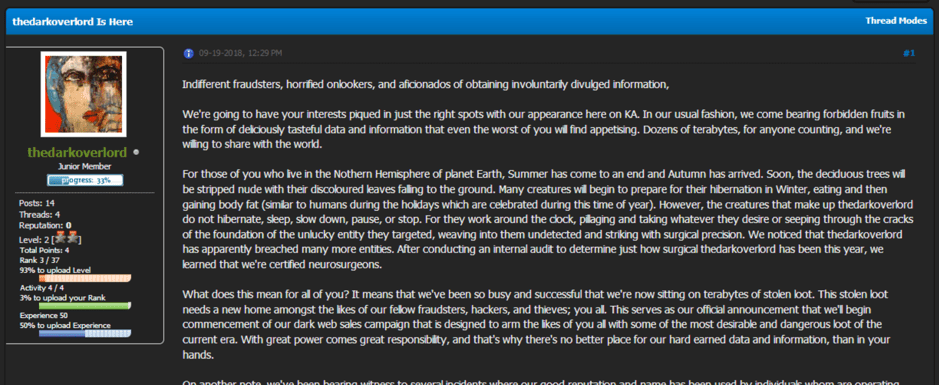
Thedarkoverlord Out to KickAss and Cash Out Their Data
September 27, 2018 | 5 Min Read
10 Things You Didn’t Know You Could Do with Shadow Search™
September 25, 2018 | 5 Min Read

ShadowTalk Update – 09.24.2018
September 24, 2018 | 3 Min Read

The 2017 FSB indictment and Mitre ATT&CK™
September 20, 2018 | 11 Min Read

Non-traditional State Actors: New Kids on the Block
September 18, 2018 | 5 Min Read

ShadowTalk Update – 09.17.2018
September 17, 2018 | 2 Min Read
Airline Discovers Trove of Frequent Flyer Accounts Compromised and Posted for Sale Online
September 14, 2018 | 3 Min Read
MITRE ATT&CK™ and the North Korean Regime-Backed Programmer
September 13, 2018 | 18 Min Read
GAO’s Equifax Post-mortem Report
September 11, 2018 | 5 Min Read

ShadowTalk Update – 09.10.2018
September 10, 2018 | 3 Min Read

Sextortion – When Persistent Phishing Pays Off
September 6, 2018 | 4 Min Read
Online Risks to Fortnite Users
September 4, 2018 | 5 Min Read

ShadowTalk Update – 09.03.2018
September 3, 2018 | 3 Min Read

Security Analyst Spotlight Series: Heather Farnsworth
August 30, 2018 | 5 Min Read

Understanding Threat Modelling
August 29, 2018 | 4 Min Read

ShadowTalk Update – 08.27.2018
August 27, 2018 | 3 Min Read
Online Cybercrime Courses: Back to School Season
August 23, 2018 | 4 Min Read

Mitre ATT&CK™ and the FIN7 Indictment: Lessons for Organizations
August 22, 2018 | 12 Min Read

ShadowTalk Update – 08.20.2018
August 20, 2018 | 3 Min Read

Five Threats to Financial Services: Part Five, Hacktivism
August 15, 2018 | 5 Min Read

Five Threats to Financial Services: Part Four, Payment Card Fraud
August 14, 2018 | 6 Min Read

ShadowTalk Update – 08.13.2018
August 13, 2018 | 3 Min Read

Digital Shadows Contributes to Insider Threat Research
August 9, 2018 | 5 Min Read

Five Threats to Financial Services: Phishing Campaigns
August 8, 2018 | 7 Min Read

ShadowTalk Update – 08.06.2018
August 6, 2018 | 2 Min Read

FIN7: Arrests and Developments
August 2, 2018 | 6 Min Read

Diversity of Thoughts in the Workplace: Are You Thinking What I’m Thinking?
August 1, 2018 | 3 Min Read

Security Spotlight Series: Dr. Richard Gold
July 31, 2018 | 4 Min Read

ShadowTalk Update – 07.30.2018
July 30, 2018 | 3 Min Read

Black Hat USA 2018
July 26, 2018 | 2 Min Read

Cyber Threats to ERP Applications: Threat Landscape
July 24, 2018 | 4 Min Read

ShadowTalk Update – 07.23.2018
July 23, 2018 | 3 Min Read

Five Threats to Financial Services: Banking Trojans
July 19, 2018 | 5 Min Read

Mitre ATT&CK™ and the Mueller GRU Indictment: Lessons for Organizations
July 17, 2018 | 10 Min Read

Digital Risk Protection: Avoid Blind Spots with a More Complete Risk Picture
July 17, 2018 | 5 Min Read

ShadowTalk Update – 07.16.2018
July 16, 2018 | 2 Min Read

Alleged Carbanak Files and Source Code Leaked: Digital Shadows’ Initial Findings
July 11, 2018 | 6 Min Read

Security Analyst Spotlight Series: Harrison Van Riper
July 10, 2018 | 6 Min Read

ShadowTalk Update – 07.09.2018
July 9, 2018 | 3 Min Read

Reducing Your Attack Surface: From a Firehose to a Straw
July 5, 2018 | 6 Min Read

ShadowTalk Update – 07.02.2018
July 2, 2018 | 3 Min Read

Diversity and Digital Shadows Women’s Network
June 26, 2018 | 3 Min Read

ShadowTalk Update – 06.25.2018
June 25, 2018 | 3 Min Read

How Cybercriminals are Using Messaging Platforms
June 21, 2018 | 4 Min Read

Five Threats to Financial Services: Part One, Insiders
June 19, 2018 | 5 Min Read

ShadowTalk Update – 06.18.2018
June 18, 2018 | 3 Min Read

Security Analyst Spotlight Series: Rafael Amado
June 14, 2018 | 9 Min Read
How Cybercriminals are using Blockchain DNS: From the Market to the .Bazar
June 12, 2018 | 5 Min Read

Shadow Talk Update – 06.11.2018
June 11, 2018 | 3 Min Read

Threats to the 2018 Football World Cup: Traditional Rules or a New Style of Play?
June 7, 2018 | 7 Min Read
Market.ms: Heir to the AlphaBay and Hansa throne?
June 4, 2018 | 5 Min Read

Shadow Talk Update – 06.04.2018
June 4, 2018 | 3 Min Read

7 Ways The Digital Risk Revolution Changes Risk and Compliance – Webinar Key Insights
May 30, 2018 | 5 Min Read

Shadow Talk Update – 05.29.2018
May 29, 2018 | 4 Min Read

Security Analyst Spotlight Series: Rose Bernard
May 23, 2018 | 5 Min Read

A New Approach for Channel Security Consultants
May 22, 2018 | 5 Min Read

Shadow Talk Update – 05.21.2018
May 21, 2018 | 3 Min Read

Digital Shadows 7th Anniversary – A Look Back
May 16, 2018 | 4 Min Read
