Year: 2019

ShadowTalk Update – Jingle Bell Ryuk: NOLA Ransomware, Ring Doorbells, and 2020 Predictions
December 23, 2019 | 3 Min Read

ShadowTalk Update – Jingle Bell Ryuk: NOLA Ransomware, Ring Doorbells, and 2020 Predictions
December 23, 2019 | 3 Min Read

Top Security Blogs of 2019 from Digital Shadows
December 20, 2019 | 4 Min Read
The Closure of Market.ms: A Cybercriminal Marketplace Ahead of Its Time
December 18, 2019 | 9 Min Read
2020 Cybersecurity Forecasts: 5 trends and predictions for the new year
December 18, 2019 | 10 Min Read

Forums are Forever – Part 3: From Runet with Love
December 17, 2019 | 24 Min Read

ShadowTalk Update – Tochka Dark Web Market Offline, Market.ms Closes, and Data Leakage Stories
December 16, 2019 | 3 Min Read

Threat Intelligence: A Deep Dive
December 12, 2019 | 21 Min Read

Forums are Forever – Part 2: Shaken, but not Stirred
December 10, 2019 | 5 Min Read

ShadowTalk Update – Cybercriminal Forum Research, Mixcloud Breach, and International Crackdown on RAT Spyware
December 9, 2019 | 3 Min Read

A Threat Intelligence Analyst’s Guide to Today’s Sources of Bias
December 5, 2019 | 9 Min Read

Forums are Forever – Part 1: Cybercrime Never Dies
December 4, 2019 | 10 Min Read
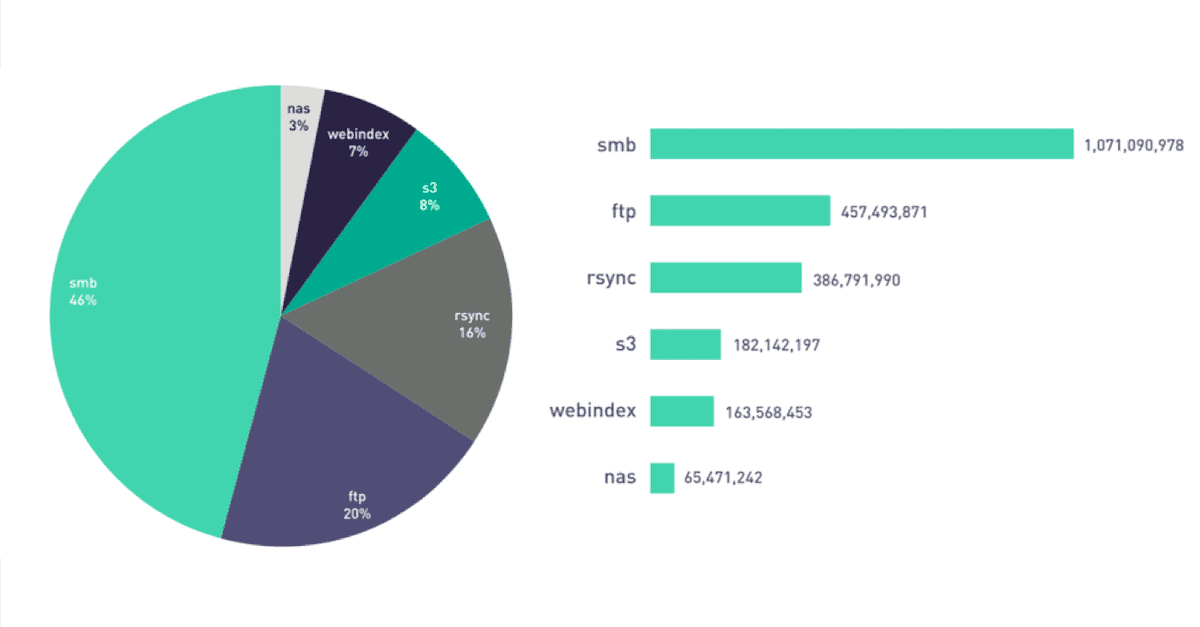
2.3 billion files exposed across online file storage technologies
December 3, 2019 | 17 Min Read

ShadowTalk Update – RIPlace, Trickbot, and Russian-language forum Probiv
December 2, 2019 | 3 Min Read
Asset Inventory Management: Difficult But Essential
November 27, 2019 | 4 Min Read
Probiv: The missing pieces to a cybercriminal’s puzzle
November 26, 2019 | 10 Min Read

ShadowTalk Update – Black Friday Deals on the Dark Web, Phineas Fisher Manifesto, and DarkMarket
November 25, 2019 | 3 Min Read

Black Friday Deals on the Dark Web: A cybercriminal shopper’s paradise
November 21, 2019 | 10 Min Read
DarkMarket’s Feminist Flight Towards Equality and the Curious Case of Canaries
November 19, 2019 | 4 Min Read

BSidesDFW 2019: OSINT Workshop Recap
November 18, 2019 | 5 Min Read

ShadowTalk Update – BSidesDFW Recap, Dynamic CVV Analysis, and the Facebook Camera Bug
November 18, 2019 | 3 Min Read
VoIP security concerns: Here to stay, here to exploit
November 14, 2019 | 4 Min Read

Dynamic CVVs: 2FA 2Furious
November 12, 2019 | 5 Min Read

ShadowTalk Update – BlueKeep Attacks, Megacortex Ransomware, and Web.com Breach
November 11, 2019 | 3 Min Read

Combatting Domain-Centric Fraud: Why Mimecast is partnering with Digital Shadows
November 7, 2019 | 3 Min Read

ShadowTalk Update – Avast Breach Attempt, NordVPN Breach, and Wifi Security Risks
November 4, 2019 | 4 Min Read
Understanding the Different Cybercriminal Platforms: AVCs, Marketplaces, and Forums
October 31, 2019 | 6 Min Read
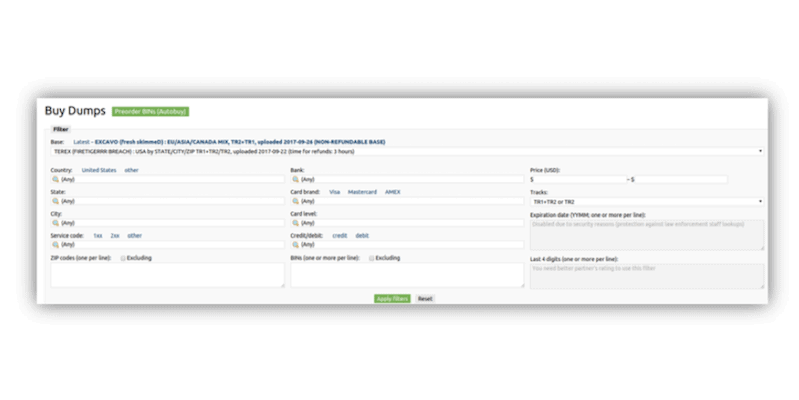
Cybercriminal credit card stores: Is Brian out of the club?
October 31, 2019 | 8 Min Read

Your Cyber Security Career – Press start to begin
October 30, 2019 | 13 Min Read

Australia Cyber Threat Landscape report (H1 2019)
October 29, 2019 | 5 Min Read

ShadowTalk Update – Avast Breach Attempt, NordVPN Breach, and Wifi Security Risks
October 25, 2019 | 3 Min Read

Understanding the Consequences of Data Leakage through History
October 24, 2019 | 4 Min Read

WiFi Security: Dispelling myths of using public networks
October 23, 2019 | 9 Min Read

Japan Cyber Threat Landscape report (H1 2019)
October 22, 2019 | 5 Min Read

ShadowTalk Update – Typosquatting and the 2020 U.S. Election, Honeypots, And Sudo Vulnerability
October 18, 2019 | 3 Min Read

Honeypots: Tracking Attacks Against Misconfigured or Exposed Services
October 17, 2019 | 9 Min Read

Typosquatting and the 2020 U.S. Presidential election: Cyberspace as the new political battleground
October 16, 2019 | 15 Min Read
Cybercriminal Forum Developments: Escrow Services
October 15, 2019 | 5 Min Read

ShadowTalk Update – Iran-linked APT35, Skimming by Magecart 4, Rancour, and Emotet Resurgence
October 11, 2019 | 3 Min Read
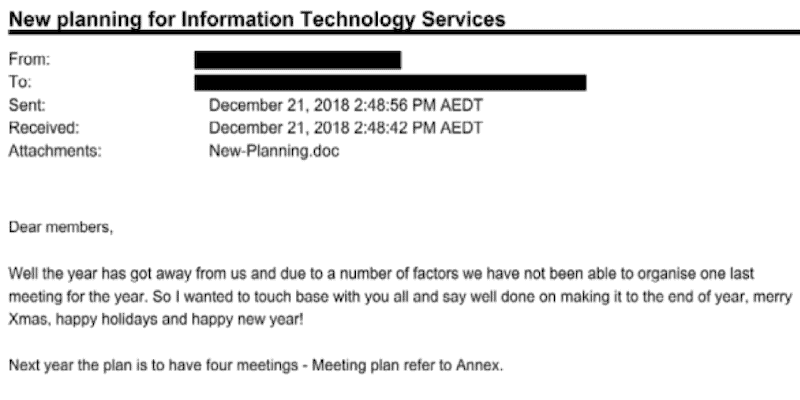
ANU Breach Report: Mapping to Mitre ATT&CK Framework
October 11, 2019 | 14 Min Read

Dark Web Overdrive: The Criminal Marketplace Understood Through Cyberpunk Fiction
October 9, 2019 | 5 Min Read

ShadowTalk Update – Magecart Five Widens Attack Vectors, Suspected Chinese Threat Actor Targets Airbus Suppliers, and Tortoiseshell Developments
October 4, 2019 | 3 Min Read

Top Threat Intelligence Podcasts to Add to Your Playlist
October 3, 2019 | 4 Min Read

Domain Squatting: The Phisher-man’s Friend
October 1, 2019 | 8 Min Read

ShadowTalk Update – Tortoiseshell Targets IT Providers, the Tyurin Indictment, and Emotet’s Return
September 27, 2019 | 4 Min Read

Singapore Cyber Threat Landscape report (H1 2019)
September 26, 2019 | 7 Min Read

Mapping the Tyurin Indictment to the Mitre ATT&CK™ framework
September 25, 2019 | 7 Min Read
DevSecOps: Continued Database Exposures Point to Growing Challenges
September 24, 2019 | 5 Min Read

ShadowTalk Update – Universities still attracting espionage from Iran, SimJacker exploit, NCSC Threat Trends, and Ransomware Updates
September 20, 2019 | 4 Min Read

Nemty Ransomware: Slow and Steady Wins the Race?
September 19, 2019 | 3 Min Read

NCSC Cyber Threat Trends Report: Analysis of Attacks Across UK Industries
September 18, 2019 | 7 Min Read

Your Data at Risk: FBI Cyber Division Shares Top Emerging Cyber Threats to Your Enterprise
September 17, 2019 | 8 Min Read

ShadowTalk Update – Metasploit Project Publishes Exploit For Bluekeep, plus APT3 and Silence Cybercrime Group Updates
September 13, 2019 | 4 Min Read

Dark Web Monitoring: The Good, The Bad, and The Ugly
September 11, 2019 | 20 Min Read
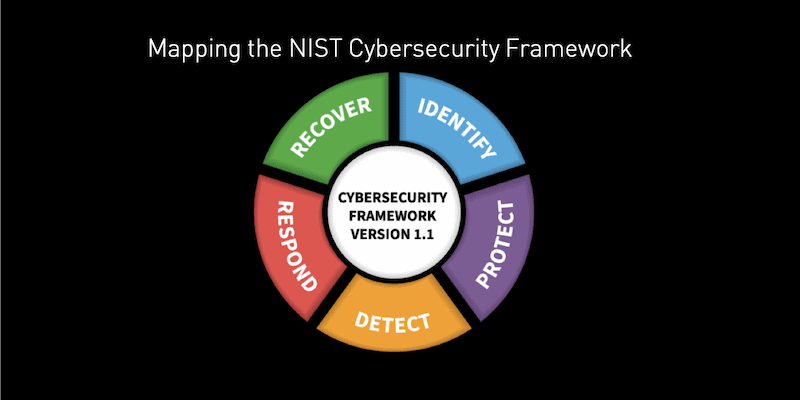
Mapping the NIST Cybersecurity Framework to SearchLight: Eating our own BBQ
September 10, 2019 | 2 Min Read

ShadowTalk Update – Ryuk Ransomware, Twitter rids SMS tweets, and Facebook Records Exposed
September 9, 2019 | 3 Min Read

Envoy on a Mission to Bring Stability to the Criminal Underground
September 4, 2019 | 3 Min Read
ShadowTalk Update – More Sodinokibi Activity, Imperva Breach, and Weirdest Food at the Texas State Fair
September 2, 2019 | 3 Min Read

Emotet Returns: How To Track Its Updates
August 26, 2019 | 5 Min Read

ShadowTalk Update – Texas Ransomware Outbreaks and Phishing Attacks Using Custom 404 pages
August 23, 2019 | 3 Min Read
Breach! An Analysis of the Modern Digital Breach, with Cyber Defense Lab’s CEO, Bob Anderson
August 22, 2019 | 8 Min Read

The Nouns of Black Hat: People, Places, and Things From Summer Camp 2019
August 19, 2019 | 6 Min Read

Black Hat and DEFCON 2019 – Some of our Favorite Sessions
August 19, 2019 | 9 Min Read

ShadowTalk Update – Nightmare Market in Disarray and SEC Investigation into Data Leak at First American Financial Corp
August 16, 2019 | 3 Min Read

Fresh blow for dark web markets: Nightmare market in disarray
August 13, 2019 | 5 Min Read

Recon Village: Panning for gold
August 1, 2019 | 7 Min Read

Capital One Breach: What we know and what you can do
July 31, 2019 | 5 Min Read

The Account Takeover Kill Chain: A Five Step Analysis
July 30, 2019 | 17 Min Read

ShadowTalk Update – More BlueKeep updates, FSB contractor hacked, and the Enigma Market
July 29, 2019 | 3 Min Read

Surviving and Thriving at Blackhat and DEF CON Summer Camp 2019
July 24, 2019 | 4 Min Read
SearchLight’s Biggest Ever Update: New Ways to Discover, Contextualize, and Prioritize Digital Risks
July 23, 2019 | 6 Min Read
A Growing Enigma: New AVC on the Block
July 19, 2019 | 3 Min Read

ShadowTalk Update – Marriott Faces GDPR Fines, TA505 Global Attacks, Zoom 0-Day, and New Magecart Activity
July 12, 2019 | 3 Min Read
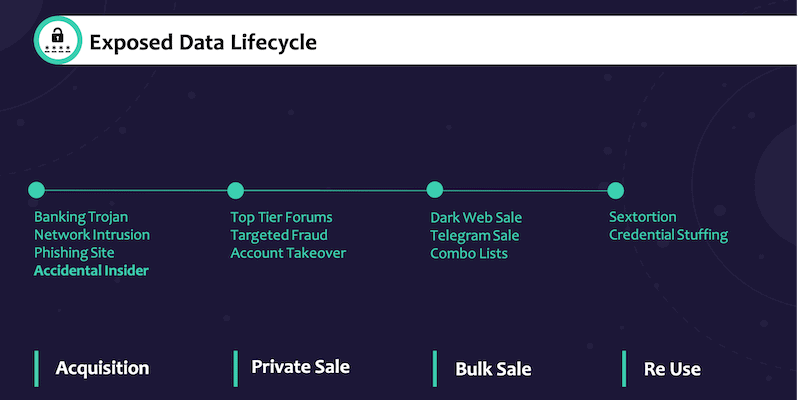
Harnessing Exposed Data to Enhance Cyber Intelligence
July 11, 2019 | 7 Min Read

Welcoming NAB Ventures & Scaling SearchLight for Growth
July 9, 2019 | 2 Min Read

Extortion, Sale, Reconnaissance, & Impersonation: 4 Ways Your Digital Footprint Enables Attackers
July 2, 2019 | 6 Min Read
ShadowTalk Update – Operation Soft Cell, Libra Cryptocurrency Impersonations, and New Cyber Espionage Activity
June 28, 2019 | 4 Min Read

Facebook’s Libra Cryptocurrency: Cybercriminals tipping the scales in their favor
June 27, 2019 | 8 Min Read
ShadowTalk Update – Google Calendar Phishing, Exim Email Server Vulnerability, and Diversity in Cybersecurity
June 24, 2019 | 3 Min Read
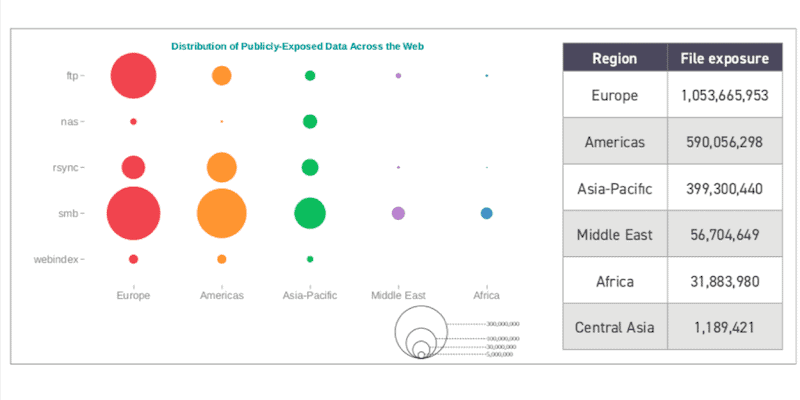
Leaky SMB File Shares – So Many Bytes!
June 19, 2019 | 5 Min Read

Managing Digital Risk: 4 Steps to Take
June 18, 2019 | 9 Min Read

ShadowTalk Update – XMRig Cryptocurrency Mining, FIN8 Backdoor, and Attacks Against Office 365
June 17, 2019 | 3 Min Read

Managing Infosec Burnout: The Hidden Perpetrator
June 10, 2019 | 8 Min Read

ShadowTalk Update – “HiddenWasp” and “BlackSquid” malware, TA505 and Turla actvity, and Too Much Information:The Sequel
June 7, 2019 | 3 Min Read

BlueKeep: Cutting through the hype to prepare your organization
May 24, 2019 | 8 Min Read
Automating 2FA phishing and post-phishing looting with Muraena and Necrobrowser
May 21, 2019 | 6 Min Read

Partnering with SecureLink to help organizations minimize their digital risk
May 15, 2019 | 3 Min Read
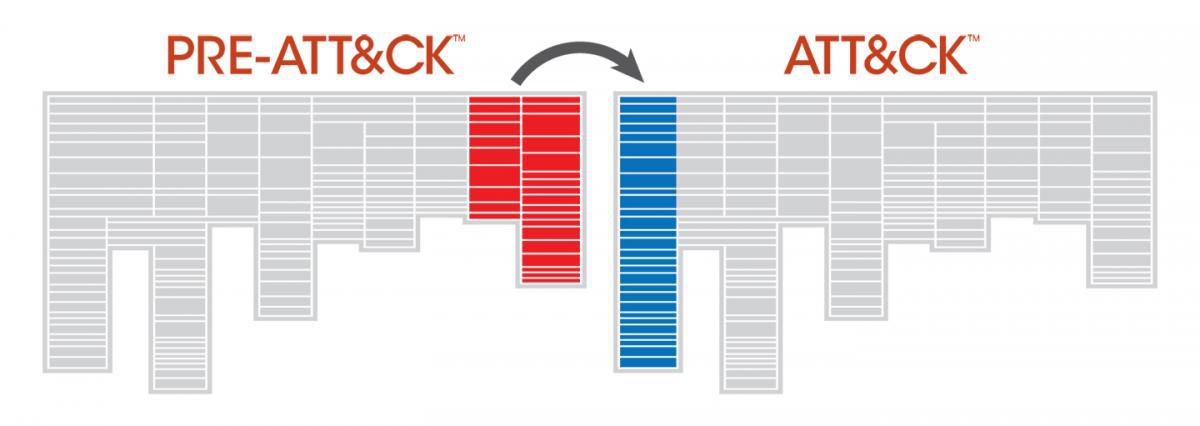
Mapping Iran’s Rana Institute to MITRE Pre-ATT&CK™ and ATT&CK™
May 15, 2019 | 15 Min Read

Cyber Talent Gap: How to Do More With Less
May 14, 2019 | 5 Min Read

ShadowTalk Update – 5.06.19
May 13, 2019 | 4 Min Read

Enabling Soi Dog’s Digital Transformation: A Case Study
May 8, 2019 | 3 Min Read

Announcing Digital Shadows’ ISO27001 certification
May 7, 2019 | 2 Min Read

ShadowTalk Update – 5.06.19
May 6, 2019 | 3 Min Read

ShadowTalk Update – 4.29.19
April 29, 2019 | 3 Min Read

FBI IC3: Cybercrime Surges in 2018, Causing $2.7 Billion in Losses
April 23, 2019 | 4 Min Read

ShadowTalk Update – 4.22.19
April 22, 2019 | 3 Min Read

ShadowTalk Update – 4.15.19
April 15, 2019 | 4 Min Read

Reducing your attack surface
April 9, 2019 | 4 Min Read

ShadowTalk Update – 4.8.19
April 8, 2019 | 3 Min Read
Easing into the extortion game
April 3, 2019 | 4 Min Read

Predator: Modeling the attacker’s mindset
April 2, 2019 | 6 Min Read
