Year: 2017

What Attackers Want for Christmas
December 22, 2017 | 4 Min Read

OL1MP: A Telegram Bot Making Carding Made Easy This Holiday Season
December 21, 2017 | 3 Min Read

‘Tis The Season To Do Predictions – The 2018 Cybersecurity Landscape
December 18, 2017 | 3 Min Read

Why I Joined Digital Shadows: Product, Culture and Opportunity
December 13, 2017 | 2 Min Read

A New CISO Looking to See How Deep the Rabbit Hole Goes
December 12, 2017 | 2 Min Read
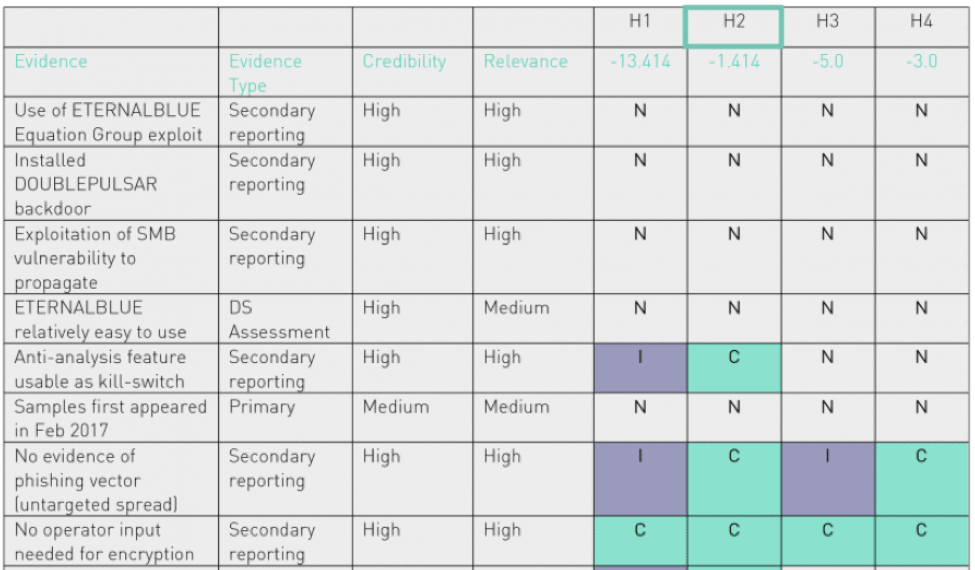
Digital Shadows’ Most Popular Blogs of 2017: Analysis of Competing Hypotheses For The Win
December 12, 2017 | 3 Min Read

Meet the New Digitalshadows.com
November 29, 2017 | 2 Min Read

Risks to Retail: Cybercriminals Sharing the Joy This Holiday Season
November 21, 2017 | 3 Min Read

GDPR – Not Just a European Concern
November 20, 2017 | 6 Min Read

Fake News is More Than a Political Battlecry
November 16, 2017 | 3 Min Read

Why “Have a Safe Trip” Is Taking On Greater Meaning
November 14, 2017 | 5 Min Read

Know Where to Find Your Digital Risk
November 10, 2017 | 4 Min Read

Pwnage to Catalonia: Five Things We Know About OpCatalunya
November 2, 2017 | 5 Min Read
ICS Security: Strawmen In the Power Station
October 31, 2017 | 5 Min Read

Extorters Going to Extort: This Time Other Criminals Are the Victims
October 26, 2017 | 3 Min Read

Women in Security: Where We Are And Where We Need To Go
October 25, 2017 | 7 Min Read

Trust vs Access: A Tale of Two Vulnerability Classes
October 20, 2017 | 5 Min Read

Key Reinstallation Attacks (KRACK): The Impact So Far
October 16, 2017 | 4 Min Read

Simply Put, Effective Cybersecurity is the Strength Sum of Its Parts
October 11, 2017 | 2 Min Read

Simple Steps to Online Safety
October 5, 2017 | 4 Min Read

Gearing Up For National Cyber Security Awareness Month
October 3, 2017 | 4 Min Read

2017 Equifax Breach: Impact and Lessons Learned
September 28, 2017 | 3 Min Read

Recognition of Hard Work and Relevance – It’s Time to Go Global
September 20, 2017 | 3 Min Read

Bringing Down the Wahl: Three Threats to the German Federal Election
September 14, 2017 | 7 Min Read

An Update on the Equifax Data Breach
September 13, 2017 | 8 Min Read

Equifax Breach: The Impact For Enterprises and Consumers
September 8, 2017 | 9 Min Read

Return of the Worm: A Red Hat Analysis
September 7, 2017 | 4 Min Read

Content Delivery Networks (CDNs) Can Leave You Exposed – How You Might be Affected and What You Can Do About It
September 6, 2017 | 5 Min Read

Bitglass: Compromised Credentials are Just One Way Your Corporate Data is Being Exposed
August 18, 2017 | 2 Min Read
Fluctuation in the Exploit Kit Market – Temporary Blip or Long-Term Trend?
August 16, 2017 | 5 Min Read

All That Twitterz Is Not Gold: Why You Need to Rely on Multiple Sources of Intelligence
August 9, 2017 | 3 Min Read

Cybercrime Finds a Way, the Limited Impact of AlphaBay and Hansa’s Demise
August 7, 2017 | 5 Min Read

Reading Your Texts For Fun and Profit – How Criminals Subvert SMS-Based MFA
August 1, 2017 | 4 Min Read

What is a Threat Model, and Why Organizations Should Care
July 31, 2017 | 4 Min Read

Fraudsters Scoring Big – an Inside Look at the Carding Ecosystem
July 18, 2017 | 3 Min Read

The Future of Marketplaces: Forecasting the Decentralized Model
July 17, 2017 | 4 Min Read

AlphaBay Disappears: 3 Scenarios to Look For Next
July 14, 2017 | 6 Min Read

Threat Led Penetration Testing – The Past, Present and Future
July 10, 2017 | 5 Min Read

Petya-Like Wormable Malware: The “Who” and the “Why”
June 30, 2017 | 7 Min Read

Keep Your Eyes on the Prize: Attack Vectors are Important But Don’t Ignore Attacker Goals
June 23, 2017 | 5 Min Read

Threats From the Dark Web
June 26, 2017 | 5 Min Read

WannaCry: An Analysis of Competing Hypotheses – Part II
June 7, 2017 | 7 Min Read

7 Tips for Protecting Against Account Takeovers
May 22, 2017 | 3 Min Read
WannaCry: An Analysis of Competing Hypotheses
May 18, 2017 | 6 Min Read

Digital Shadows’ 6th Anniversary
May 16, 2017 | 5 Min Read

5 Lessons from WannaCry: Preventing Attacks with Security Engineering
May 16, 2017 | 5 Min Read

WannaCry: The Early 2000s Called, They Want Their Worms Back
May 12, 2017 | 3 Min Read

Authentication Nation: 5 Ways NIST is Changing How We Think About Passwords
May 9, 2017 | 4 Min Read

The 3 Pillars of Digital Risk Management: Part 3 – The Top 5 Main Risks of Reputational Damage
April 27, 2017 | 2 Min Read

The Usual Suspects: Understanding the Nuances of Actors’ Motivations and Capabilities
April 21, 2017 | 3 Min Read

Liberté, égalité, securité: 4 Threats to the French Presidential Election
April 20, 2017 | 5 Min Read

The 3 Pillars of Digital Risk Management: Part 2 – The 6 Main Areas That Contribute to Data Leakage Risks
April 18, 2017 | 2 Min Read
The 3 Pillars of Digital Risk Management: Part 1 Understanding Cyber Threats
April 13, 2017 | 3 Min Read

All Sources Are Not the Same; Why Diversity Is Good for Intelligence
April 11, 2017 | 3 Min Read

Monitoring the Mobile Threat Landscape
April 4, 2017 | 4 Min Read

OpIsrael Hacktivists Targeted By Unknown Threat Actor
March 30, 2017 | 3 Min Read

Turk Hack Team and the “Netherlands Operation”
March 29, 2017 | 4 Min Read

Tax Fraud in 2017
March 27, 2017 | 4 Min Read

Dutch Elections – Looking Back at Cyber Activity
March 21, 2017 | 3 Min Read

Five Reasons Why Alex Seton VP of Business and Corporate Development, Joined Digital Shadows
March 21, 2017 | 3 Min Read

5 Risks Posed By Mobile Applications That SearchLight Helps You Manage
March 14, 2017 | 2 Min Read

Back to the red pencil – Cyber threats to the Dutch elections
March 13, 2017 | 5 Min Read

Learning from the Top Threats Financial Services Faced in 2016
March 8, 2017 | 2 Min Read
New “Blaze” exploit kit claims to exploit recent Cisco WebEx vulnerability
March 2, 2017 | 4 Min Read

Step by Step: The Changing Face of Threat Led Penetration Testing
February 28, 2017 | 4 Min Read

Sun to Set on BEPS/Sundown Exploit Kit?
February 22, 2017 | 4 Min Read

Four Things to Look Out for This Valentine’s Day
February 14, 2017 | 4 Min Read

An unusually Swift(tay) malware delivery tactic
February 9, 2017 | 5 Min Read
F3EAD: Find, Fix, Finish, Exploit, Analyze and Disseminate – The Alternative Intelligence Cycle
February 8, 2017 | 4 Min Read
How the Frenzy Unfolded: Analyzing Various Mongo Extortion Campaigns
February 7, 2017 | 4 Min Read

Ready for the Blitz: Assessing the Threats to Super Bowl LI
February 2, 2017 | 4 Min Read

Making Cents of ATM Malware Campaigns – Comparing and Contrasting Operational Methodologies
January 30, 2017 | 4 Min Read

Dial “M” for malware: Two-factor scamming
January 26, 2017 | 4 Min Read

Innovation in The Underworld: Reducing the Risk of Ripper Fraud
January 23, 2017 | 7 Min Read
Known Unknowns: Key Events to Keep Your Eyes Out for in 2017
January 19, 2017 | 3 Min Read

Two Ways to Effectively Tailor Your Intelligence Products
January 17, 2017 | 4 Min Read

All You Can Delete MongoDB Buffet
January 12, 2017 | 4 Min Read

10 Ways You Can Prepare for DDoS Attacks in 2017
January 11, 2017 | 1 Min Read

Trump and Intelligence: 6 Ways To Deal With Challenging Intelligence Consumers
January 4, 2017 | 4 Min Read
