Year: 2016

Mirai: A Turning Point For Hacktivism?
December 16, 2016 | 5 Min Read
Coming to a Country Near You? The Rapid Development of The TrickBot Trojan
December 16, 2016 | 4 Min Read
Crowdsourced DDoS Extortion – A Worrying Development?
December 13, 2016 | 3 Min Read

You Should Consider Forecasts, Not Predictions
December 9, 2016 | 4 Min Read

The Top Three Most Popular Blogs of 2016
December 8, 2016 | 2 Min Read

A Model of Success: Anticipating Your Attackers’ Moves
December 1, 2016 | 4 Min Read

Windows Shopping: 7 Threats To Look Out For This Holiday Season
November 23, 2016 | 5 Min Read
Ransomware-as-a-service: The Business Case
November 22, 2016 | 4 Min Read

Leak on Aisle 12! An Analysis of Competing Hypotheses for the Tesco Bank Incident
November 11, 2016 | 5 Min Read

Top 5 Threats to the Media and Broadcasting Industry
November 11, 2016 | 3 Min Read

Surveying the Criminal Market
November 8, 2016 | 3 Min Read

Overexposed and Under-Prepared; The Risks of Oversharing Online
November 8, 2016 | 4 Min Read

Five Tips For Better Email Security
November 8, 2016 | 4 Min Read
Resilience: Adapt or Fail
October 28, 2016 | 5 Min Read
Anonymous Poland – Not Your Typical Hacktivist Group
October 28, 2016 | 4 Min Read

Don’t Break the Internet, Fix Your Smart Devices
October 25, 2016 | 4 Min Read

Rocking the Vote? The Effects of Cyber Activity On The U.S. Election
October 25, 2016 | 5 Min Read
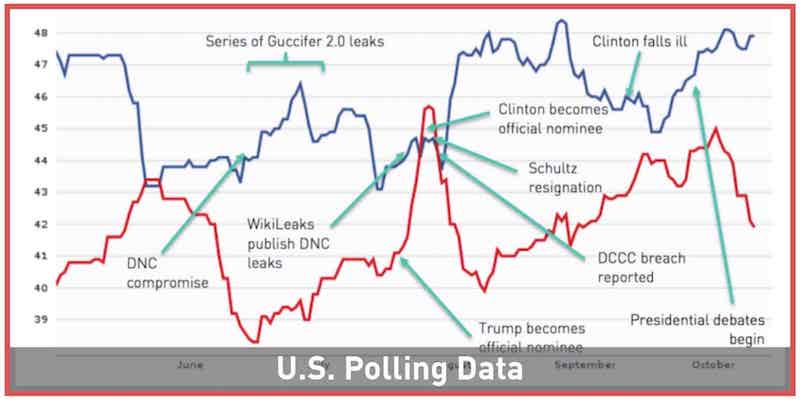
Targeting of Elections; Old News, Fresh Tactics
October 25, 2016 | 4 Min Read

Squashing Domain Squatting
October 24, 2016 | 6 Min Read

Combatting Online Crime With “Needle-Rich Haystacks”
October 18, 2016 | 3 Min Read

4 Tricks to Make a Cybersecurity Training a Treat
October 12, 2016 | 3 Min Read

Digital Risk Monitoring Is A Service, Not a Distinct Capability
October 11, 2016 | 2 Min Read

Balancing the Scales: The PRC’s Shift to Symmetrical Engagement
October 6, 2016 | 4 Min Read

Do Not Invite Them In: What “Human Error” Can Mean In Practice
October 6, 2016 | 4 Min Read

Plumbing the Depths: the Telnet protocol
October 3, 2016 | 4 Min Read

Swotting Up On Exploit Kit Infection Vectors
October 3, 2016 | 3 Min Read

Phishful Of Dollars: BEC Remains Top Of The Charts
October 3, 2016 | 3 Min Read
Five Tips To Make Your Passwords Better
September 26, 2016 | 4 Min Read

Digital Risk Monitoring Can Negate ‘Indicators of Exhaustion’
September 26, 2016 | 2 Min Read

The Industrialized Uses of Breached Data
September 21, 2016 | 4 Min Read

Beauty and the Breach: Leaked Credentials in Context
September 21, 2016 | 4 Min Read
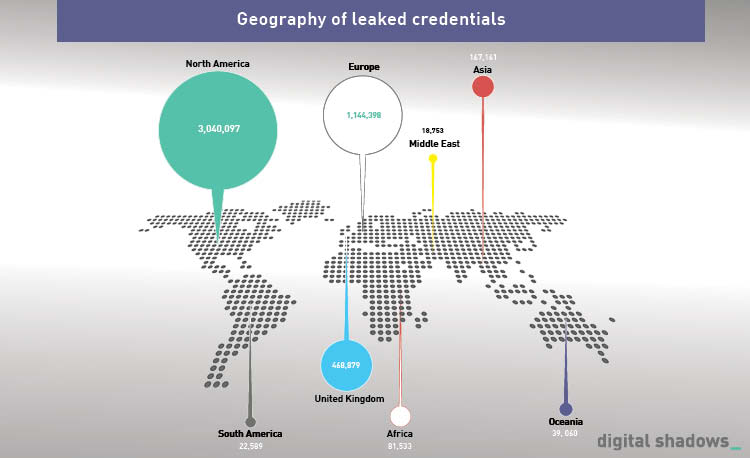
New report: 97 percent of the top 1,000 companies suffer from credential compromise
September 20, 2016 | 2 Min Read

Three easy tips to staying safe online
September 19, 2016 | 4 Min Read

Forecasting the exploit kit landscape
September 15, 2016 | 5 Min Read

Understanding Exploit Kits’ Most Popular Vulnerabilities
September 12, 2016 | 2 Min Read

Hacktivism, it’s not all DoSing around
September 12, 2016 | 4 Min Read

Show me the context: The hacking proof of concept
September 8, 2016 | 2 Min Read

The cyber defender and attacker imbalance – a disproportionate impact
September 6, 2016 | 3 Min Read

Hybrid cyber/physical criminal operations – where network intrusions meet the physical world
August 30, 2016 | 3 Min Read

Bozkurt to Buhtrap: Cyber threats affecting financial institutions in 1H 2016
August 23, 2016 | 3 Min Read

Four Things We’ve Learned From the Alleged Equation Group Code Leak
August 22, 2016 | 4 Min Read

Security Culture: You’re only as strong as your team
August 18, 2016 | 4 Min Read
False flags in cyber intrusions – why bother?
August 17, 2016 | 3 Min Read

Forecasting OpOlympicHacking
August 15, 2016 | 3 Min Read

“Air cover” – cybercriminal marketing and the media
August 10, 2016 | 3 Min Read

Overexposure – photos as the missing link
August 3, 2016 | 3 Min Read

More Data Leaks as part of OpOlympicHacking
July 28, 2016 | 2 Min Read

Gambling with Security in Vegas: Not Your Best Bet
July 27, 2016 | 4 Min Read

Getting In Gear: Accounting for Tactical and Strategic Intelligence
July 26, 2016 | 3 Min Read

Thedarkoverlord – losing his patients?
July 26, 2016 | 4 Min Read

5 Takeaways From The “Building A Strategic Threat Intelligence Program” Webinar
July 26, 2016 | 3 Min Read

Tracking the Field: Eight cybersecurity considerations around Rio 2016
July 25, 2016 | 2 Min Read
PoodleCorp: in the business of kudos
July 22, 2016 | 5 Min Read

Towards a(nother) new model of attribution
July 21, 2016 | 4 Min Read

5 Key Lessons From The FDIC’s Breach Disclosure Debacle
July 18, 2016 | 4 Min Read

Open Source Intelligence versus Web Search: What’s The Difference?
July 11, 2016 | 4 Min Read

Three Tactics Behind Cyber Extortion
July 11, 2016 | 3 Min Read

Modern crimeware campaigns – two bytes of the cherry
July 5, 2016 | 3 Min Read

10 ways to prepare for credential leak incidents
June 30, 2016 | 2 Min Read

Recycling, bad for your environment!
June 27, 2016 | 4 Min Read

The philosophical difference between the Old and New Schools of the cybercriminal underground
June 27, 2016 | 3 Min Read

Spidey-sense for the people
June 23, 2016 | 5 Min Read

Forecasting the implications for cybersecurity in Britain after Thursday’s referendum
June 21, 2016 | 4 Min Read

Shining a light on the dark web
June 21, 2016 | 3 Min Read

Standoff in cyberspace
June 17, 2016 | 3 Min Read

OPSEC versus branding – the cyber criminal’s dilemma
June 17, 2016 | 3 Min Read

“Hidden” TeamViewer service advertised on criminal forum
June 17, 2016 | 5 Min Read

Your money or your data: Keeping up-to-date with the innovation
June 17, 2016 | 2 Min Read

Inconsistencies in Intelligence Collection
June 17, 2016 | 4 Min Read

Are you at risk from business email compromise?
June 6, 2016 | 3 Min Read

Hacktivism: same old, same old?
June 3, 2016 | 4 Min Read

Building an Intelligence Capability: Agility, Creativity and Diversity
June 2, 2016 | 2 Min Read

The OPSEC Opportunity
May 31, 2016 | 2 Min Read

Are you certain you know what risk means?
May 31, 2016 | 5 Min Read

Data breaches targeting financial services: 2016 so far
May 26, 2016 | 3 Min Read

The Plan is Mightier than the Sword – Re(sources)
May 24, 2016 | 3 Min Read

The Plan is Mightier than the Sword – Persistence
May 24, 2016 | 5 Min Read

The Plan is Mightier than the Sword – Planning
May 24, 2016 | 4 Min Read

OpIcarus – Increased Claims Against Financial Institutions
May 23, 2016 | 3 Min Read

Goliath ransomware, giant problem or giant con?
May 17, 2016 | 3 Min Read

Bozkurt Hackers continue to leak bank data
May 13, 2016 | 4 Min Read

Digital Shadows – The Innovation Continues
May 13, 2016 | 2 Min Read

Analyzing the 2016 Verizon Data Breach Investigations Report
May 2, 2016 | 4 Min Read
Getting Strategic With Your Threat Intelligence Program
April 26, 2016 | 4 Min Read

Roboanalyst: The Future of Threat Intelligence?
April 25, 2016 | 3 Min Read

The Hacking Team breach – an attacker’s point of view
April 22, 2016 | 3 Min Read

OpIsrael: An Update
April 6, 2016 | 3 Min Read

URGENT, ACT. RQD: Navigating Business Email Compromise
April 4, 2016 | 3 Min Read

Dark web: More than just a bastion of criminality
March 31, 2016 | 3 Min Read

It’s time to put the diligence into your M&A due diligence
March 29, 2016 | 2 Min Read

Cybersecurity for the nuclear industry – ‘in service modification’ or more systemic change required?
March 29, 2016 | 4 Min Read

Online credit card shops – a numbers game
March 21, 2016 | 3 Min Read

Antifragile Security: Bouncing Back Stronger
March 21, 2016 | 3 Min Read

Moar Sand!
March 10, 2016 | 3 Min Read

Uncertainties in the Language of Uncertainty – and why we need to talk about it
February 25, 2016 | 4 Min Read

Intelligence vs. Infosec: The 3-letter-guy to the rescue?
February 25, 2016 | 3 Min Read

From cyber espionage to hacker marketing strategies: an overview of Digital Shadows talks at RSA Conference
February 25, 2016 | 2 Min Read

WHAT DO YOU MEAN IT WAS AN ACCIDENT?
February 25, 2016 | 4 Min Read
We always want to find someone or something to pin the blame on when a serious data breach occurs. But is it really that...
The ‘hacker’ talent shortage: What organizations can learn from the recruitment efforts of their attackers
February 24, 2016 | 5 Min Read

Using News Reports as a Source of Intelligence
February 23, 2016 | 4 Min Read
