Year: 2020
Top Three SearchLight Updates in 2020
December 28, 2020 | 3 Min Read

A Christmas 2020 Review: Confronting and controlling insider threats
December 21, 2020 | 6 Min Read

QUO, QUO, QUO! Merry Christmas…..
December 21, 2020 | 7 Min Read

How Bizarre: Joker’s Stash .bazar site allegedly seized by law enforcement
December 17, 2020 | 6 Min Read
Top Five ShadowTalk Episodes of the Year
December 17, 2020 | 4 Min Read

Holiday Cybercrime: Krampus is in Town
December 15, 2020 | 7 Min Read

SolarWinds Compromise: What security teams need to know
December 14, 2020 | 5 Min Read
Digital Shadows’ Top Five Blogs of 2020
December 10, 2020 | 6 Min Read
Impersonator Syndrome: Supply chain lures and COVID-19 cures
December 9, 2020 | 3 Min Read

How Cybercriminals Answer “What do you do for a living?”
December 3, 2020 | 8 Min Read
The Top 3 Cybersecurity Threats In The Middle East
December 2, 2020 | 7 Min Read

2021 Forecasts: Six Trends And Predictions For The New Year
December 1, 2020 | 18 Min Read
ShadowTalk Update: Egregor Ransomware, IoT Regulations, Black Friday Threats and More!
November 30, 2020 | 2 Min Read
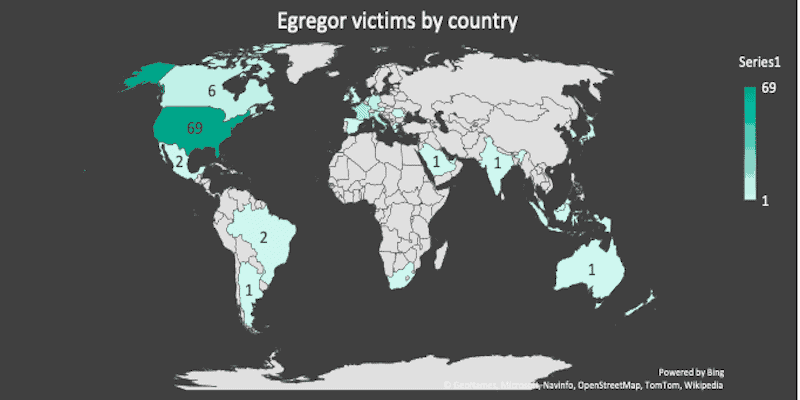
Egregor: The New Ransomware Variant to Watch
November 24, 2020 | 9 Min Read
SearchLight’s Exposed Document Alerts: Uncover the Critical, Faster
November 23, 2020 | 5 Min Read

Holiday Cybercrime: Retail Risks and Dark Web Kicks
November 19, 2020 | 7 Min Read
ShadowTalk Update: RegretLocker, OceanLotus, Millions Seized in Cryptocurrency, and more!
November 16, 2020 | 2 Min Read

To Code or Not to Code? Cybercriminals and the world of programming
November 12, 2020 | 9 Min Read
Work Smarter, Not Harder: The Evolution of DDoS Activity in 2020
November 10, 2020 | 10 Min Read

A Eulogy for Maze: The end of a ransomware era?
November 9, 2020 | 6 Min Read

Simplifying Cybercriminal Jargon: A Glossary of Cybercriminal Access Offerings
November 2, 2020 | 15 Min Read
Ransomware operators targeting healthcare organizations: Monitoring the situation
October 29, 2020 | 9 Min Read

Mapping MITRE ATT&CK to SandWorm APT’s Global Campaign
October 28, 2020 | 7 Min Read

Cybersecurity Awareness Month: Week 4 – The Future of Connected Devices
October 28, 2020 | 8 Min Read

Foreign cyber threats to the 2020 US presidential election
October 27, 2020 | 12 Min Read
Marcus Carey Joins ShadowTalk
October 23, 2020 | 3 Min Read
Dark pathways into cybercrime: Minding the threat actor talent gap
October 21, 2020 | 11 Min Read

Cybersecurity Awareness Month: Week 3 – Securing Internet- Connected Devices in Healthcare
October 21, 2020 | 9 Min Read
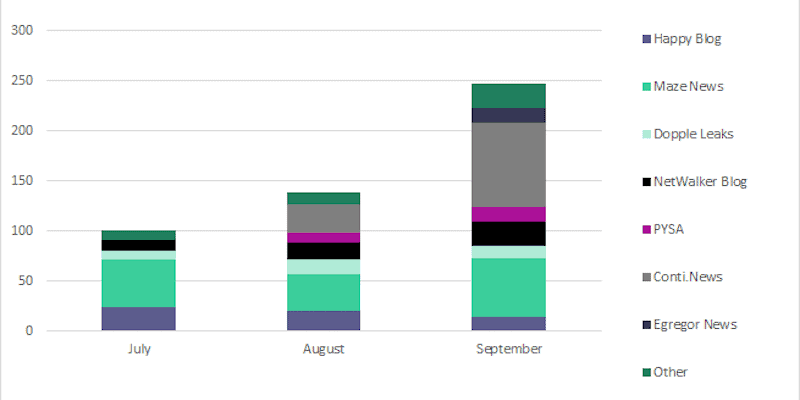
Quarterly Update: Ransomware Trends in Q3
October 19, 2020 | 8 Min Read

Digital Shadows Analysis of Europol’s Cybercrime Report
October 14, 2020 | 12 Min Read

Cybersecurity Awareness Month: Week 2 – Security Devices at Home and Work
October 14, 2020 | 7 Min Read

Clickbait to Checkmate: SMS-based scam targets US smartphones and accesses victim locations
October 13, 2020 | 11 Min Read

Cybersecurity Awareness Month: Week 1 – If you Connect It, Protect It
October 8, 2020 | 6 Min Read
Help your development teams keep their keys safe
October 7, 2020 | 3 Min Read
Let’s get ready to tumble! Bitcoin vs Monero
October 6, 2020 | 13 Min Read

Recent arrests and high-profile convictions: What does it mean for the cyber threat landscape?
September 30, 2020 | 13 Min Read
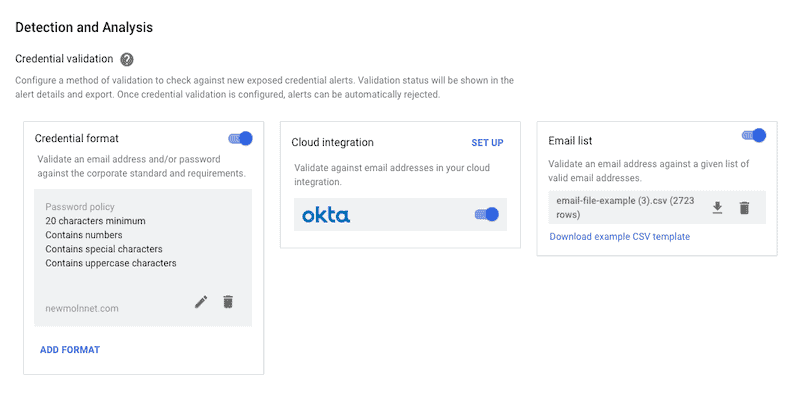
Four Ways to Validate Credentials in SearchLight
September 29, 2020 | 3 Min Read
Cybercriminals Targeting SAP RECON
September 29, 2020 | 5 Min Read
Unpicking Cybercriminals’ Personalities – Part 2: Morality and Forum Dynamics
September 28, 2020 | 7 Min Read
ShadowTalk Update – Law Enforcement Cracks Down On Cybercriminals, Fancy Bear Goes Phishing, And More
September 28, 2020 | 2 Min Read
RECAP: Discussing deception with Chris Sanders
September 24, 2020 | 3 Min Read

Unpicking Cybercriminals’ Personalities – Part 1: Gender and Nationality
September 23, 2020 | 9 Min Read
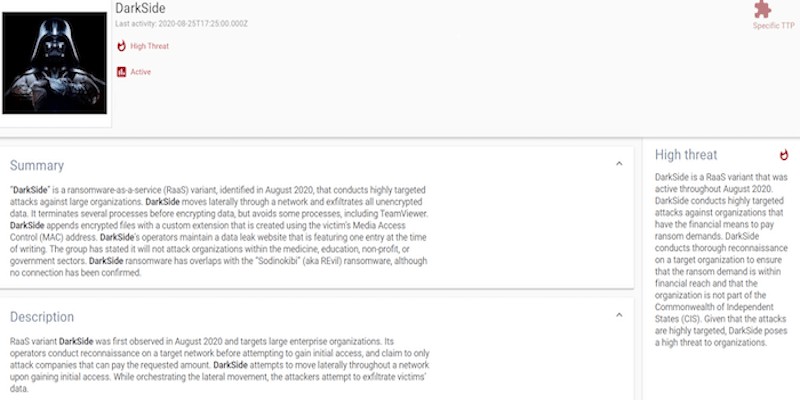
DarkSide: The new ransomware group behind highly targeted attacks
September 22, 2020 | 8 Min Read

ShadowTalk Update – Ed Merrett Joins To Talk HackableYou And The Latest In Threat Intel
September 21, 2020 | 2 Min Read

With the Empire falling, who will take over the throne?
September 16, 2020 | 10 Min Read
Access Keys Exposed: More Than 40% Are For Database Stores
September 14, 2020 | 6 Min Read
ShadowTalk Update – The Team Talks Baka, Epic Manchego, and Smaug, Plus Emotet Rides Again
September 14, 2020 | 2 Min Read
Recruitment fraud: Don’t spook your dream candidates this halloween
September 10, 2020 | 4 Min Read
Not another ransomware blog: Initial access brokers and their role
September 9, 2020 | 5 Min Read

Cyber espionage: How to not get spooked by nation-state actors
September 8, 2020 | 8 Min Read
ShadowTalk Update – New Zealand Stock Exchange faces DDoS, Tesla avoids cyberattack, and Pioneer Kitten updates
September 7, 2020 | 2 Min Read

Revisiting Typosquatting and the 2020 US Presidential Election
September 2, 2020 | 11 Min Read
What is DevSecOps and Why Do We Need It?
August 12, 2020 | 4 Min Read
Dread takes on the spammers – who will come out on top?
August 28, 2020 | 9 Min Read

Fall of the behemoth: Cybercriminal underground rocked by Empire’s apparent exit scam
August 27, 2020 | 10 Min Read

“ALEXA, WHO IS THE NUMBER ONE CYBERCRIMINAL FORUM TO RULE THEM ALL?”
August 26, 2020 | 12 Min Read
RECAP: Discussing the evolution and trends of cybercrime with Geoff White
August 25, 2020 | 8 Min Read

Validate Exposed Credentials with Okta to Save Even More Time
August 24, 2020 | 3 Min Read
ShadowTalk Update – Emotet Gets a Vaccine, NSA Drovorub Advisory, and North Korean Activity plus Bureau 121
August 24, 2020 | 3 Min Read
Dark Web Forums: The new kid on the block
August 18, 2020 | 12 Min Read
Optiv CTIE 2020: COVID-19, cybercrime, and third-party risk
August 17, 2020 | 10 Min Read
ShadowTalk Update – Defaced Subreddits, Intel Leak Drama on Twitter, and HIBP Goes Open-Source
August 17, 2020 | 2 Min Read
It’s even easier to initiate takedowns in SearchLight
August 12, 2020 | 3 Min Read
Escrow systems on cybercriminal forums: The Good, the Bad and the Ugly
August 11, 2020 | 15 Min Read
ShadowTalk Update – CWT pays ransom, data leaked for 900+ Pulse Secure Servers, EU issues first cyber sanctions
August 10, 2020 | 2 Min Read

Saving the SOC from overload by operationalizing digital risk protection
August 5, 2020 | 4 Min Read

The story of Nulled: Old dog, new tricks
August 4, 2020 | 9 Min Read
BitBazaar Market and The Rise of Neptune Market: The End of the Saga spells hope for another
August 3, 2020 | 8 Min Read
ShadowTalk Update – Garmin ransomware attack, QSnatch malware, and ShinyHunters Stage 2
August 3, 2020 | 3 Min Read

Dark Web Travel Agencies Revisited: The Impact of Coronavirus on the Shadow Travel Industry
July 29, 2020 | 10 Min Read
Account takeover: Expanding on impact
July 27, 2020 | 7 Min Read

ShadowTalk Update – Trickbot trojan mishaps, Emotet resurgence, Twitter takeovers, and APT group updates
July 27, 2020 | 2 Min Read
Ransomware Trends in Q2: How Threat Intelligence Helps
July 22, 2020 | 8 Min Read
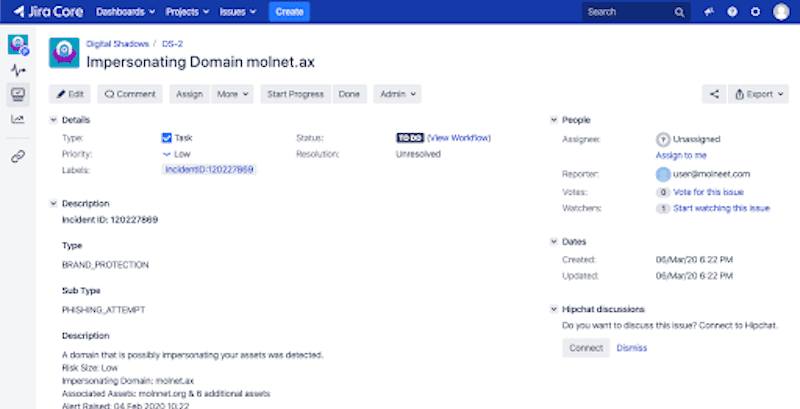
Jira Atlassian SearchLight Integration
July 21, 2020 | 2 Min Read

The Rise of OpenBullet: A Deep Dive in the Attacker’s ATO toolkit
July 20, 2020 | 9 Min Read

Abracadabra! – CryptBB demystifying the illusion of the private forum
July 15, 2020 | 8 Min Read
SearchLight’s Credential Validation: Only Focus on What Matters
July 14, 2020 | 4 Min Read
Tax Fraud in 2020: Down But Not Out
July 13, 2020 | 4 Min Read

ShadowTalk Update – PAN-OS Vulnerability, Lazarus Group, BEC scammer “Hushpuppi”, and New Photon ATO Research
July 13, 2020 | 2 Min Read

From Exposure to Takeover: Part 1. Beg, borrow, and steal your way in
July 7, 2020 | 9 Min Read

Digital Risk Reporting Best Practices: Top 10 Ways to Build Killer Reports in SearchLight
June 30, 2020 | 4 Min Read
Multiple vs. Exclusive Sales on the Dark Web: What’s in a sale?
June 29, 2020 | 9 Min Read
ShadowTalk Update – Torigon, Nulledflix, and BlueLeaks, Plus DevSecOps Insights From DS CISO Rick
June 29, 2020 | 2 Min Read

Introducing Nulledflix – Nulled forum’s own streaming service
June 23, 2020 | 8 Min Read
Torigon Forum: A sad case of all show and no go
June 23, 2020 | 11 Min Read
Modern Software Development and DevSecOps: Despite security controls, data leaks persist
June 22, 2020 | 15 Min Read

ShadowTalk Update – Lookback Operators Deploy New Malware Against US Utilities Sector And Honda Cyber Attack
June 22, 2020 | 2 Min Read
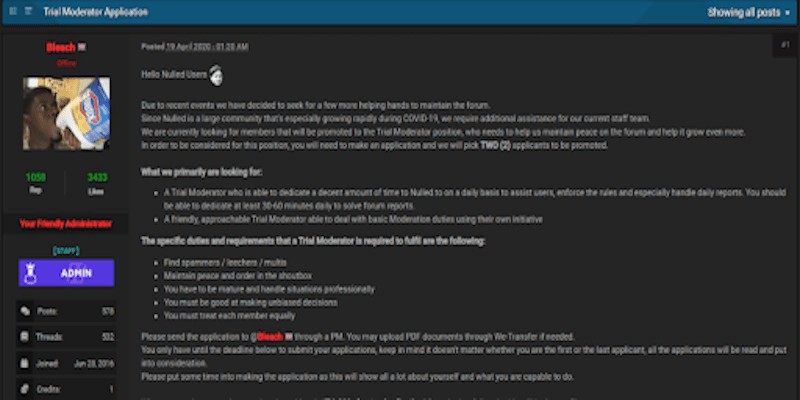
Ensuring order in the underground: Recruiting moderators on cybercriminal forums
June 18, 2020 | 10 Min Read
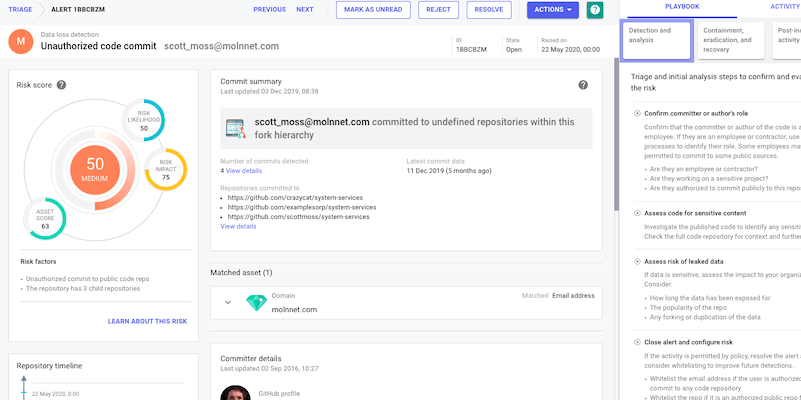
Reducing technical leakage: Detecting software exposure from the outside-in
June 16, 2020 | 6 Min Read
ShadowTalk Update – Maze Ransomware Alliance, EndGame DDoS Protection Tool, And Ransomware Disguises
June 15, 2020 | 2 Min Read
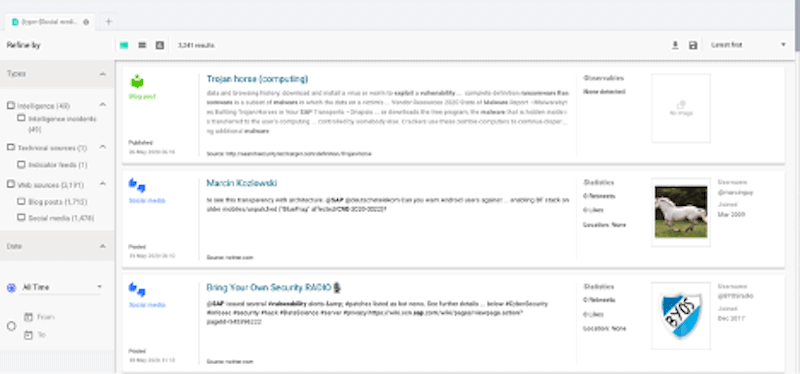
Security Threat Intel Products and Services: Mapping SearchLight
June 10, 2020 | 6 Min Read

CISA and FBI alert: Top vulnerabilities exploited from 2016-2019 and trends from 2020
June 9, 2020 | 7 Min Read
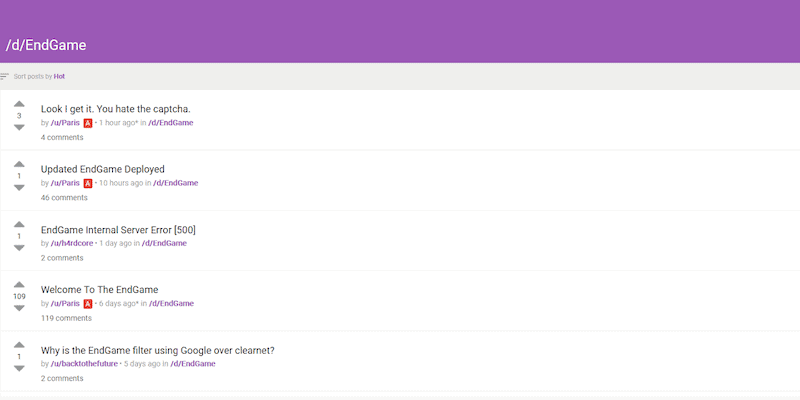
New DDoS protection tool advertised on the dark web
June 9, 2020 | 7 Min Read
SHADOWTALK UPDATE – HACKTIVIST CHOOSES DESTRUCTION OVER PROFIT W/ RANSOMWARE AND COLLECTION 1 HACKER IDENTIFIED
June 1, 2020 | 2 Min Read

Dark Web Digest: Exploring the risk impact of dark web findings, the evolution of forums, and observed trends
May 29, 2020 | 12 Min Read
3 Phishing Trends Organizations Should Watch Out For
May 20, 2020 | 16 Min Read

The 2020 Verizon Data Breach Investigations Report: One CISO’s View
May 19, 2020 | 6 Min Read
SHADOWTALK UPDATE – WANNACRY ANNIVERSARY, WORDPRESS PLUGIN VULNERABILITY, AND WELEAKDATA COMPROMISED
May 18, 2020 | 2 Min Read

A NEW DECADE OF CYBER THREATS: LOOKING BACK AT THE TRENDING CYBER TOPICS OF Q1 2020
May 14, 2020 | 10 Min Read
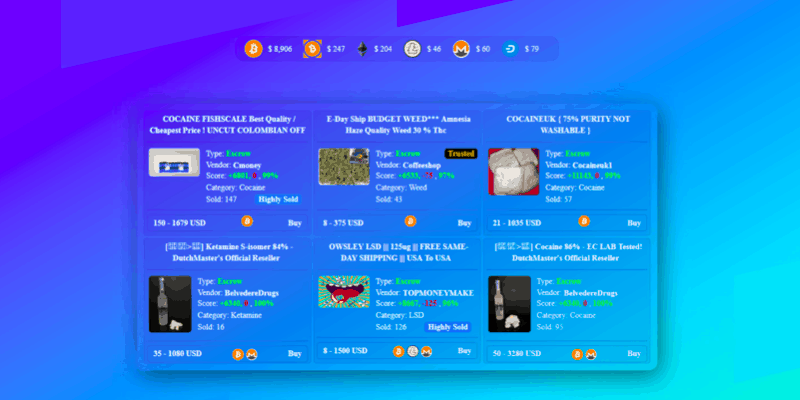
BitBazaar Market: Deception and Manipulation on the Dark Web
May 12, 2020 | 8 Min Read
