Year: 2021

ShadowTalk Year in Review: Top 5 Episodes of 2021
December 30, 2021 | 3 Min Read
AlphaBay’s Return: A slow-burning masterpiece, or a flash in the pan?
December 28, 2021 | 4 Min Read

Year in Review: Our Top Blogs of 2021
December 23, 2021 | 9 Min Read

Log4j: Tokyo Drift
December 22, 2021 | 5 Min Read
US Ban on Huawei: Is this the right approach?
December 22, 2021 | 7 Min Read

Discord: Do You Need to Be Concerned This Christmas?
December 21, 2021 | 7 Min Read
Log4j: What’s Happened Since
December 15, 2021 | 5 Min Read
Cone of Plausibility: Forecasting Ransomware Scenarios in 2022
December 14, 2021 | 10 Min Read

The Log4j Zero-Day: What We Know So Far
December 10, 2021 | 6 Min Read
Latin American Financial Services: Sunny Climes and Cybercrimes
December 9, 2021 | 8 Min Read
2021: An APAC Cyber-security Odyssey
December 8, 2021 | 9 Min Read

Outside the Perimeter: The New Digital Risk Landscape
December 7, 2021 | 6 Min Read
Cyber Threats to Government
December 2, 2021 | 3 Min Read

When acting turns criminal: Deepfakes and voice impersonators in the cybercriminal underground
December 1, 2021 | 13 Min Read
To Disclose, or Not to Disclose: The PoC Dilemma
November 30, 2021 | 6 Min Read
The Patching Nightmare
November 24, 2021 | 7 Min Read

Black Friday: Is there a threat actor in your shopping cart?
November 23, 2021 | 9 Min Read
Emotet is back again: what does it mean?
November 16, 2021 | 4 Min Read

Vulnerability Intelligence: What’s the Word in Dark Web Forums?
November 16, 2021 | 7 Min Read
What is Vulnerability Intelligence?
November 11, 2021 | 6 Min Read

Vulnerable smart contracts and fake blockchains: What do investors need to know?
November 10, 2021 | 10 Min Read
What We’re Reading This Month
November 9, 2021 | 6 Min Read
Initial Access Brokers in Q3 2021
November 3, 2021 | 9 Min Read

Managing your External Attack Surface with SearchLight
November 2, 2021 | 4 Min Read

ENISA 2021 Threat Landscape: Initial Thoughts
November 1, 2021 | 12 Min Read
REvil Dead, And Other Spooky Security Tales
October 27, 2021 | 6 Min Read

Cybersecurity Awareness Month: Week 4 – Cybersecurity first (…middle and last)
October 26, 2021 | 6 Min Read

Ransomware Q3 Roll Up
October 25, 2021 | 11 Min Read

What Is Intellectual Property Protection?
October 20, 2021 | 2 Min Read

Cybersecurity Awareness Month: Week 3 – Explore. Experience. Share
October 19, 2021 | 11 Min Read

REvil Domains Hijacked, Forum Representative Announces Group’s Intention to Go Offline
October 18, 2021 | 5 Min Read
Strategic Threat Intelligence and You: What Does It All Mean?
October 14, 2021 | 4 Min Read

Cybersecurity Awareness Month: Week 2 – Fight the Phish!
October 13, 2021 | 9 Min Read

What is Third Party Risk?
October 6, 2021 | 3 Min Read
Cybersecurity Awareness Month: Week 1 – Managing Your Digital Shadow
October 5, 2021 | 8 Min Read

What We’re Reading This Month: September Edition
September 29, 2021 | 8 Min Read

Tactical Threat Intelligence and You: What Does It All Mean?
September 29, 2021 | 5 Min Read
Why CISOs and Executives Should Care About IABs
September 23, 2021 | 3 Min Read

Data Leakage Detection Best Practices
September 22, 2021 | 3 Min Read

Ukrainian-language Cybercriminal Platforms: A Gap In the Market?
September 21, 2021 | 7 Min Read

Building successful teams on the cybercriminal underground
September 15, 2021 | 7 Min Read

Enhance Executive Protection with SocialMonitor
September 14, 2021 | 3 Min Read

SearchLight Leads the Digital Risk Protection Market
September 10, 2021 | 3 Min Read

AlphaBay’s Return: SWOT Findings
September 9, 2021 | 14 Min Read

What We’re Reading This Month
September 8, 2021 | 6 Min Read
Protecting Against Ransomware: What Role Does Threat Intelligence Play?
September 7, 2021 | 4 Min Read

Preventing Ransomware: Preventing the 300 at Thermopylae
September 2, 2021 | 7 Min Read

Social Media Monitoring Best Practices
September 1, 2021 | 3 Min Read
The Never-ending Ransomware Story
August 31, 2021 | 10 Min Read
The Eeveelution of ShinyHunters: From Data Leaks to Extortions
August 26, 2021 | 7 Min Read

How Cybercriminals Weaponize Social Media
August 25, 2021 | 9 Min Read
No Honor Among Thieves: Scamming the Scammers
August 24, 2021 | 5 Min Read
Leveraging Digital Shadows’ Premium Services
August 18, 2021 | 3 Min Read

The Phight Against Phishing
August 17, 2021 | 17 Min Read
The (Nation) State of APTs in 2021
August 12, 2021 | 10 Min Read

Understanding Smishing Attacks
August 10, 2021 | 5 Min Read

How Has Forum Life Adapted to the Recent Ransomware Ban?
August 5, 2021 | 8 Min Read
Supply Chain Attacks in 2021: It Takes a Village
August 4, 2021 | 10 Min Read
Initial Access Brokers in Q2
August 3, 2021 | 7 Min Read
REvil: Analysis of Competing Hypotheses
July 28, 2021 | 15 Min Read

Getting Started With Domain Monitoring Part 3: Remediation
July 27, 2021 | 5 Min Read
SearchLight Reduces Domain Triage by 75%
July 21, 2021 | 5 Min Read
Cyber Threats to the Tokyo 2020 Olympic Games
July 21, 2021 | 8 Min Read

Q2 Ransomware Roll Up
July 20, 2021 | 9 Min Read

REvil Ransomware: What’s Next?
July 15, 2021 | 10 Min Read
Kaseya Attack Update: What’s Happened Since?
July 14, 2021 | 6 Min Read

Why Domains Matter: Impersonations and Your Brand
July 13, 2021 | 9 Min Read
Marketo: A Return to Simple Extortion
July 8, 2021 | 9 Min Read
Getting Started with Domain Monitoring Part 2: Detection
July 7, 2021 | 4 Min Read
Kaseya Ransomware Supply-Chain Attack: What We Know So Far
July 5, 2021 | 7 Min Read
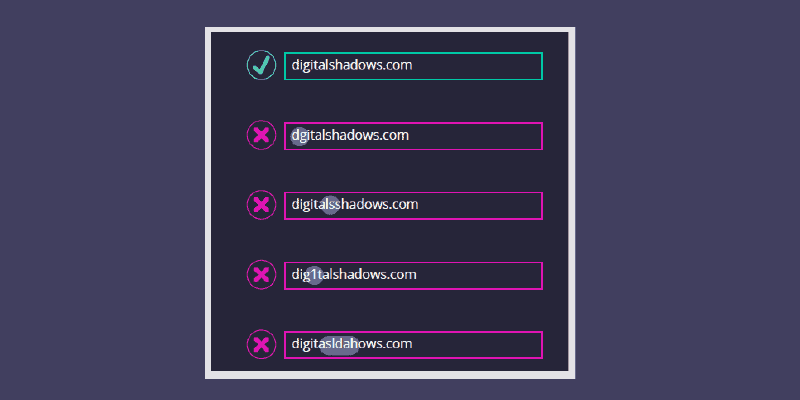
Typosquatting Protection 101
July 1, 2021 | 6 Min Read
Getting Started with Domain Monitoring: Part 1, Collection
June 30, 2021 | 4 Min Read

What We’re Reading This Month
June 29, 2021 | 6 Min Read
Why Do Users Get Banned from Cybercriminal Forums?
June 24, 2021 | 13 Min Read

Threat Actors Living Off the Land
June 23, 2021 | 10 Min Read

Let’s Talk About Intel Requirements
June 17, 2021 | 7 Min Read

Key Findings from our Dark Web Monitoring Webinar
June 16, 2021 | 3 Min Read

Cyber Threats to the Online Gaming Industry
June 15, 2021 | 5 Min Read

Cyber Threats to the UEFA EURO 2020 Championship
June 9, 2021 | 7 Min Read
The Business of Extortion: How Ransomware Makes Money
June 9, 2021 | 8 Min Read
Cryptocurrency Attacks to be Aware of in 2021
June 8, 2021 | 10 Min Read

On the Rise: Ransomware and the Legal Services Sector
June 3, 2021 | 8 Min Read
The Top Three Cybercrime Takeaways from the 2021 Verizon DBIR
June 2, 2021 | 4 Min Read
Cyber Attacks: The Challenge of Attribution and Response
June 1, 2021 | 11 Min Read

What We’re Reading This Month
May 26, 2021 | 6 Min Read
Death and Decay: How Cybercriminal Platforms Meet Their End
May 26, 2021 | 12 Min Read
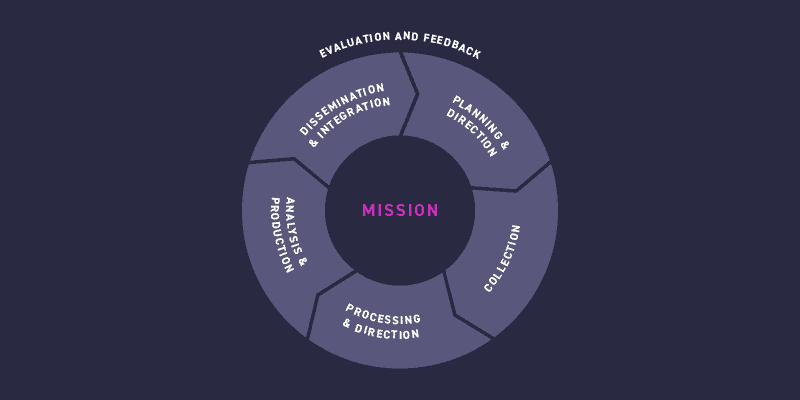
How the Intelligence Cycle Can Help Defend Against Ransomware Attack
May 25, 2021 | 14 Min Read
Ransomware-as-a-Service, Rogue Affiliates, and What’s Next
May 20, 2021 | 7 Min Read

10 Milestones Celebrating 10 Years of Digital Shadows
May 19, 2021 | 6 Min Read

Examining Russian-language Cybercriminal Marketplaces
May 18, 2021 | 10 Min Read

Colonial Pipeline Attack Update: Cybercriminal forum XSS, Exploit and RaidForums ban all things ransomware
May 14, 2021 | 8 Min Read
How Cybercriminals Can Leverage Your Vaccination Card Selfie
May 13, 2021 | 6 Min Read
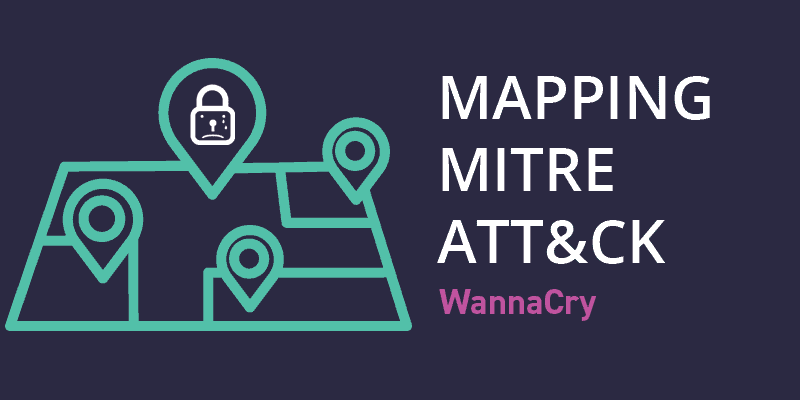
Mapping MITRE ATT&CK to the WannaCry Campaign
May 12, 2021 | 8 Min Read

Bitcoin and Alternative Cryptos in the Cybercriminal Underground
May 11, 2021 | 10 Min Read

Colonial Pipeline Ransomware Attack: What we know so far
May 10, 2021 | 5 Min Read

Creating Security-Aware Passwords
May 6, 2021 | 8 Min Read

The Top 5 Dark Web Monitoring Use Cases
May 5, 2021 | 7 Min Read
The Technology Adoption Lifecycle of Genesis Market
May 4, 2021 | 5 Min Read
Tracking Ransomware within SearchLight
April 29, 2021 | 4 Min Read
The Dark Web Response to COVID Vaccinations
April 28, 2021 | 8 Min Read
